Thursday - March 12, 2015
Thursday - March 12, 2015
Well of course
I mean, come on. WTH were you expecting?
Stirred by the controversy surrounding Hillary Clinton’s use of a private email server when she was secretary of state, a determined band of hackers, IT bloggers, and systems analysts have trained their specialized talents and state-of-the-art software on clintonemail.com, the domain under which Clinton established multiple private email accounts, and uncovered serious lapses in security, according to data shared with Fox News.
… working with publicly available tools that map network connectivity, experts have established that the last “hop” before the mail server’s Internet Protocol, or IP, address (listed as 64.94.172.146) is Internap’s aggregator in Manhattan (listed as 216.52.95.10).
“This is a very strong indication that the clintonemail.com server is in Manhattan,” the source told Fox News.
By entering the IP address for the Internap aggregator into existing databases, the experts obtained the exact geolocation coordinates for the aggregator – revealed to be on lower Broadway, at the intersection with Chambers Street, some two blocks north of City Hall. This in turn suggests that the Clinton server itself lies within close proximity – most likely former President Clinton’s Harlem office, and not as far away as the Clintons’ home in Chappaqua, N.Y.
That outside experts could so swiftly unearth such information left them convinced that the server remains, as presently configured, highly “vulnerable” to unauthorized intrusion – even if, as most observers suspect, the server, with so much publicity now attendant on it, is no longer in active use. The hackers further concluded that Clinton’s email operation was likely not much better secured when she was secretary of state.
Perhaps most concerning, private analysts determined that clintonemail.com has been running an older model of Microsoft Internet Information Services, or IIS – specifically version 7.5, which has been documented to leave users exposed on multiple fronts. The website CVEDetails.com, which bills itself as “the ultimate security vulnerability datasource,” is awash with descriptions of serious security vulnerabilities associated with version 7.5, including “memory corruption,” “password disclosure vulnerability,” and the enabling of “remote attackers to execute arbitrary code or cause a denial of service.”
The cyberlab technician who discovered the Clintons’ use of version 7.5 marveled at “the vulnerabilities the Clintons are ignoring” in an email to Fox News. “This is a big deal and just the thing real-world hackers look for in a target and will exploit to the max,” the source said.
“Several of these vulnerabilities have been known since 2010 and yet HRC is running official State comms through it.”
All this plus off the shelf generic encryption, when she could have had the very best the NSA could develop. That is, if her email server as Secretary of State was done officially, properly, and legally. Nope. It’s in Bill’s office in Harlem. I’ve got my fingers crossed hoping it’s not out in the hallway or the waiting room, and at least behind a door or two with a lock. Instead of, you know, guarded by a squad of armed U.S. Marines and a hornet’s nest of sensors and alarms.
Golly, in this day and age, it almost makes you wonder if this was set up as Swiss cheese to begin with, just in case she “needed” to have been hacked at some point in the future. Games within games? I wouldn’t put that past Hillary, would you?
And am I the only one who finds this whole thing just too damn convenient, like all those laptops issued to government flunkies that just happen to get stolen the moment they’re somehow improperly loaded up with millions of citizen’s secure records?
Arrest the wicked witch and take away her ruby shoes!!
Posted by Drew458
Filed Under: • Computers and Cyberspace • Hildabeast •
• Comments (3)
 Tuesday - January 06, 2015
Tuesday - January 06, 2015
Isn’t This Interesting.
One wonders why we don’t trust the Government anymore. (note: I’ve twice taken an oath to protect and defend the Constitution; not the government.)
Raytheon Riot Software Predicts Behavior Based on Social Media
Sounds like George Orwell’s 1984. I think he got it right… except for the year.
Here’s a quote I find especially chilling:
Last year, there were reports that the FBI was turning to social media to track stock fraud. Earlier in the year, the agency said it was developing a social media monitoring application, but insisted it would protect the privacy of individuals and protected groups before being used.
‘Protected’ groups? Who decides?
Posted by Christopher
Filed Under: • Big Brother • Computers and Cyberspace • Democrats-Liberals-Moonbat Leftists • Obama, The One • Science-Technology •
• Comments (3)
 Sunday - December 14, 2014
Sunday - December 14, 2014
Saved By My Impatience*
I’ve got some bit of wonderware running on this PC, watching over me and keeping me safe from the bad outside world full of viruses, trojans, bad clusters, fragmented files, and grubby Windows registry entries.
Most of the time Advanced SystemCare Ultimate just runs in the background, only interrupting me 3 or 5 times a day to do minor database update downloads. And then I bring the tool up every other day or so to run an in-depth file scan and a windows tune-up/junk dump/malware scan. Takes a few minutes, big deal. So I did one the other day, and when it got to the Windows Update (aka Vulnerability Fix) it just sat there. And sat there. And sat there.
Eventually I grew impatient and forced a reboot. Which caused a warning message like “If you reboot now, you may loose Windows Update 12 of 15! Wait? Y/N” and I was all, Och, tohellwiddit!, and forced the reboot. So Windows restarts, and the restart takes a sidestep while Windows shows me a “Windows is finishing installing the most recent updates” screen, which quickly stalls on update 12 of 15. This time I hit the power switch. I am the master here, you, machine, will do as you are told!!! So on the reboot of the reboot, it wanted to launch in Safe Mode but I wouldn’t let it, so it left me a message that I had Windows updates waiting to be installed. Fine. Whatevs. When I get to it beyotch.
So tonight I get an email from this left wing guy I subscribe to. Yes, I’m on the left’s mailing lists. Well, a couple of them. Not all, not by far. This guy is mostly centrist, and only gets rabid and foamy around the gums once in a while. Mostly I just delete him, but today he sent out a warning about Windows. And he was right.
Microsoft messed up the other day, and issued a bad update on December 10th. Update KB3004394 can give you problems, especially if you need to install new drivers for advanced graphics cards. It can also cause Windows to hassle you about Authenticity on start-up.
Microsoft fixed the problem immediately, issuing an update patch that removes the bad update and replaces it with the proper bit of code. This patch is update KB3024777. Both were done through the automatic update feature of Windows (which I have permanently turned off), through manual update efforts, or through middleware system protection/management tools like my Advanced SystemCare.
The good news is that this only applied to 32 bit versions of Windows 7, SP2, with some sort of Server setting I think? Whatever ... it does not apply AT ALL to Windows 8, and it was not on my Windows 7 Pro 64 bit OS. Whether because I coincidentally stopped it, or because it was not a Win Pro update, or whatever. I never had the bad update, and I never got the patch for it. Happy me.
Check to see if you have the update. It’s simple to do: Open Control Panel, select Programs, from there select Programs And Features, from there select Installed Updates. Look down to the Windows Update list, and see what you have that’s dated December 10, 2014 or newer.
Here are two links - the first tells you the story, the second is the download page for the patch from Microsoft.
http://www.pcworld.com/article/2859120/windows-7-users-urged-to-uninstall-broken-update-that-wreaks-havoc-on-software.html
http://www.microsoft.com/en-us/download/details.aspx?id=45305
There ya go. Even a lefty can be right about some things, even if it’s non-political tech. Maybe there’s some hope for us after all.
* If this was a left wing hippie site, I’d do anything I could to make this a flower power story so I could change the title to Saved By My Impatiens. hohoho. hurhurhur. I think it’s past my bedtime.
Posted by Drew458
Filed Under: • Computers and Cyberspace •
• Comments (2)
 Wednesday - November 19, 2014
Wednesday - November 19, 2014
I’m an idiot!
It was so simple to fix.
Been haunted with internet dropping on me. Took 5-10 minutes each time to recover. Had the ATT tech out twice for this. No joy. While they could see the problem they could not fix it. Even left me a spare modem. (shhhh! Not supposed to do that.)
I finally took a close look at my modem. Power? Check. Telephone? Check. What’s this third line? Unplugged it and no problem.
Posted by Christopher
Filed Under: • Computers and Cyberspace • Editorials •
• Comments (4)
 Sunday - October 05, 2014
Sunday - October 05, 2014
possible 83 million accounts are hacked at jp morgan
According to another source ... the figure is higher. It’s reported that the number is 83 million. But which ever one is correct, it is a very serious breach.
I can imagine the panic and frustration of account holders.
US bank JPMorgan has admitted that a cyber attack disclosed back in August was much more serious than at first thought, with as many as 76 million households and seven million businesses affected.
The bank said in an SEC filing that contact information such as name, address, phone number and email address had been exposed in the attack, as well as unspecified “internal JPMorgan Chase information relating to such users.”
However, it was at pains to point out that “there is no evidence” that bank account information was compromised, and it claimed that so far it has not seen any “unusual customer fraud” related to the incident.
“JPMorgan Chase customers are not liable for unauthorized transactions on their account that they promptly alert the Firm to,” it added
“The Firm continues to vigilantly monitor the situation and is continuing to investigate the matter. In addition, the Firm is fully cooperating with government agencies in connection with their investigations.”
News first emerged back in August that JPMorgan and four other banks had been hacked by a group of Russian cybercriminals, although at the time it estimated that only around one million accounts had been affected.
The new revelations make this data breach one of the worst of its kind ever.
Check Point UK managing director, Keith Bird, warned customers to be aware of potential phishing attacks in the wake of the breach.
“Attackers will try and trick customers affected by the breach into revealing more details, such as account numbers and passwords,” he added
“For the attackers, it’s just a numbers game, but it could have serious consequences for customers. Phishing emails continue to be the most common source for social engineering attacks.”
Chris Boyd, malware intelligence analyst at Malwarebytes, claimed the data stolen is a “spammer’s gold mine”
“If any of the 76 million affected have had other data leaked in the past, it would be easy for those behind this attack to build up a robust picture of their targets and throw a little social engineering into the mix, making the emails seem less random and the phone calls more persuasive,” he added.
Tim Erlin, director of IT security and risk at Tripwire, argued that other banks should take this opportunity to look at their own cyber defenses.
“While there’s little doubt that JP Morgan has taken action since the original incident was reported, the size and complexity of their network means they are unlikely to have rolled out new protections comprehensively by now,” he added.
“In situations like this, time is always the enemy.”
I can’t even imagine myself ever being savvy enough tech wise, to completely understand how things like this are done.
You’d really have to understand code and computers etc. I wouldn’t know enough to hack my own pc.
Don’t get me wrong. I have no problem regarding understanding computers and how they work.
No problem at all.
I’m fine with computers.
Until I turn one on. Once booted though ... ah well. All bets are off.
Posted by peiper
Filed Under: • Computers and Cyberspace • Crime •
• Comments (1)
 Tuesday - September 09, 2014
Tuesday - September 09, 2014
A Week of Annoyance
Well, it got to be that time again. Time for me to go on the attack, and unsubscribe from as many emailers as possible. It seems I have to do this every 2 or 3 years, or else my inbox gets buried in garbage.
It took me a few minutes a day for about a week or 10 days. Every time I had a junk mail, I looked through it until I found the Unsubscribe button down at the bottom. They all worked, except for the Orbitz one I think it was.
So I’ve drastically reduced my daily email volume. Good. Who has the time to waste? Personally, I don’t care if Yahoo or whoever is willing to let me have a Tb for free. I don’t want to have 53,000 emails. I’ve used the same home email address since 1999, and my main Inbox has just one page of opened emails in it. Everything else either gets filed in its own folder if it’s significant, or else gets the toss. Sure, I read the stuff friends and relatives send. And I reply to them. And sometimes refer back. But after a couple weeks, the “well the crops are a-growin’ here down on the farm. If’n we had a bit more rain things’d be lookin’ a mite more hopeful, but as long as Jinny the mule is still with us...” emails loose their urgency, and can get tossed. File the ones with recipes, needed phone numbers, and pictures.
Got to avoid being under the digital avalanche.
One of these days I’ll have to do the same with the BMEWS mailboxes. I get an awful lot of junk mail and spam there too.
Posted by Drew458
Filed Under: • Computers and Cyberspace •
• Comments (1)
 Saturday - August 30, 2014
Saturday - August 30, 2014
I see you
Pretty neat.
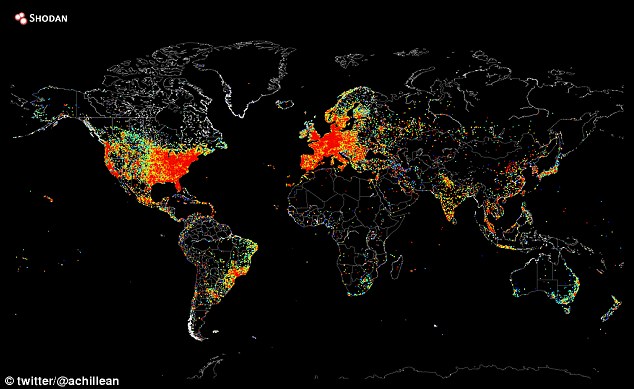
Map reveals EVERY connected device in the world
The internet has revolutionised the way we communicate and a third of the world’s population use it to stay connected.
Now, Texas-based internet cartographer and computer scientist John Matherly has used software to ‘ping’ all of these global web devices and create a map demonstrating the technology’s global reach.
In the majority of cases, this signal was sent to routers rather than individual gadgets, but Mr Matherly said iPhone and Android devices have appeared previously.
The cartographer said it took around five hours to ping all IP addresses on August 2. The map then took more than 12 hours to create.
‘Pinging’ an IP address involves sending a signal to the device from a server, which causes the connection to ‘light up’ - albeit not physically.
Mr Matherly is founder of Shodan, a search engine for connected devices.
Different colours represent the density of devices in that region, and unsurprisingly, the world’s largest cities in developed countries glow the brightest.
I think this is pretty amazing. Not only did his software ping every device on the planet, it did the job in just 5 hours. Wow. Much larger maps at the link.
And look at that one poor sod up in the middle of Greenland. Probably trying to surf up walrus porn or something. Lonely!
Posted by Drew458
Filed Under: • Computers and Cyberspace •
• Comments (0)
 Monday - August 11, 2014
Monday - August 11, 2014
A Bit Of Privacy?

If you are concerned about being internet privacy, here’s a search engine that you might like. Duckduckgo.com has a simple interface up front, and search algorithms as good as the other guys in the back. It appears to be pretty capable ...
The overhauled engine can now return videos, images, definitions, local places, and Knowledge Graph-like bursts of basic biographical information—dubbed “instant answers"—when you search for topics, all via an attractive image-driven carousel at the top of the results.
...
Plus, the icon is cute. So add this one to your list perhaps; there are more ways to hunt things up online than just Google, Bing, and DogPile. DogPile, however, was the only one that could find the real name of my favorite model The Girl With 100 Names (GW100N), who is now doing fashion work under three new aliases.
Posted by Drew458
Filed Under: • Computers and Cyberspace •
• Comments (2)
 Friday - June 27, 2014
Friday - June 27, 2014
Duct Tape is the answer
H/T to Vilmar
Heard about the NSA doing this some months ago. That’s why my computer cam has duct tape on it.
Posted by Christopher
Filed Under: • Big Brother • Computers and Cyberspace • Democrats-Liberals-Moonbat Leftists •
• Comments (0)
 Friday - April 11, 2014
Friday - April 11, 2014
Heartbleed vulnerability

Change your passwords. Right now.
No, you don’t need to change your password here at BMEWS.
But at a lot of other places, you do. Facebook. Yahoo. Google. OkCupid. Maybe your online banks and credit card sites.
Follow this link to the list of popular places impacted.
Actually, as long as you can keep track of them, it wouldn’t kill you to change as many other passwords as you have. We should all get in the habit of changing them every other month or so. Sure, right.
An encryption flaw called the Heartbleed bug is already being called one of the biggest security threats the Internet has ever seen. The bug has affected many popular websites and services — ones you might use every day, like Gmail and Facebook — and could have quietly exposed your sensitive account information (such as passwords and credit card numbers) over the past two years.
But it hasn’t always been clear which sites have been affected. Mashable reached out some of the most popular social, email, banking and commerce sites on the web. We’ve rounded up their responses below.
Some Internet companies that were vulnerable to the bug have already updated their servers with a security patch to fix the issue. This means you’ll need to go in and change your passwords immediately for these sites. Even that is no guarantee that your information wasn’t already compromised, but there’s also no indication that hackers knew about the exploit before this week. The companies that are advising customers to change their passwords are doing so as a precautionary measure.
Then go and read “How to protect yourself” over here, which pretty much tells you to change all your passwords. But to wait until the vulnerable sites have issued an “all clear” that they’ve installed a patch.
The good news is that this seems to be limited to “secure” sites, which all start with that “https” instead of “http”.
Posted by Drew458
Filed Under: • Computers and Cyberspace •
• Comments (0)
 Wednesday - December 18, 2013
Wednesday - December 18, 2013
a tech story …. mostly.
I am using Safari browser at the moment. Seems to be a bit faster than it was a while back when I stopped using it. But today, for some reason, both Chrome and FF seem to act as tho being dragged to an execution.
I happened upon this item when looking for a movie and read about this guy. I know some of you folks are very tech savvy and know all kinds of things and so may be familiar with him. But till a few days ago, I never heard of him or his story. Yeesh. Depressing, but hey. If he’s happy I should not care one way or another. For a guy who says he isn’t a gambler, what was he thinking keeping his life savings in a safe at his home?
Take a look at this.
Ron Wayne: The Apple founder who missed out on a fortuneAs a new film tells the story of a partner in a tech firm who quits and misses out on billions, Tim Walker meets the Apple co-founder Ron Wayne, who left the company after just 12 days – and so passed up on a potential fortune of $50bn
By Tim Walker
The forgotten founding partner has become a recurring character in the history of Silicon Valley – think Eduardo Saverin of Facebook, or Noah Glass of Twitter – but few such figures left their flourishing start-ups voluntarily. The exception is 79-year-old Ron Wayne. Wayne was the third man in the room on the day Steve Jobs and Steve Wozniak created Apple Computers. If he’d held on to his 10 per cent of the company, he could be worth more than $50bn. Instead, almost four decades later, Jobs is an icon, Wozniak is fabulously wealthy, and Wayne lives on his monthly social security cheque in a small town not far from Las Vegas. Unlike Flomm, however, he insists he has few regrets.
Wayne, a self-taught engineer from Ohio, was already in his forties by 1975, when he was appointed chief draftsman for product development at Atari, the videogame manufacturer behind Pong. It was at Atari’s Silicon Valley HQ that he met a twenty something Jobs, then a consulting engineer to the firm. They had shared interests, and Jobs was impressed by Wayne’s streamlining of the company’s internal documentation system .
In March 1976, Jobs came to Wayne with a request. He and his friend Steve Wozniak had developed a working design for a personal computer, which Jobs was eager to turn into a business. But he was having trouble convincing the laid-back Wozniak not to use the circuitry he’d designed for Apple elsewhere. “He was trying to get Woz to understand that the circuit was proprietary to Apple,” Wayne explains. “But Jobs was not the most diplomatic guy in the world.” On 1 April, Wayne invited the two younger men to his apartment, where he’d agreed to explain the issue to Wozniak as “the grown-up in the room”. With his intervention, Wayne says Woz quickly came around. “Jobs was sufficiently impressed by my diplomatic skills that he immediately said, ‘We’re going to form a company’.”
Jobs and Wozniak both took 45 per cent shares in the company, while Wayne held the remaining 10 per cent – and thus the balance of power. Wayne even designed the firm’s first logo, which Jobs liked enough to have it blown up into a banner to hang over their very first convention booth. And yet, 12 days after that fateful meeting, Wayne quit Apple altogether.
Though he believed in the product and thought Apple would be a success, Wayne explains that he was concerned about the implications of failure. Several years previously, he had established his own company making slot machines for Las Vegas casinos, which had quickly gone belly-up. Moreover, as the only partner with real means – “Jobs and Woz didn’t have two nickels to rub together” – he was the one with the most to lose if Apple went the same way.
“Those two guys had skills and capabilities far beyond anything I could hope to achieve, and I didn’t want to spend the next 20 years in a back office shuffling papers. So I went back to Atari, and off to the rest of my life.”
For Jobs and Wozniak, the rest is history. Wayne, meanwhile, passed the last 16 years of his career as the chief engineer of a small military electronics company. Upon retiring in 1999, he bought a large house in Florida, but soon afterwards his life savings were stolen from the safe in his garage. He was forced to sell the house and settle in Nevada. Until 1995, he didn’t even own a computer, and it took him until 2011 to acquire his first Apple product: an iPad, given to him by the organisers of a tech event in Brighton.
The last time Wayne saw Jobs was in 2000, when he was invited to an Apple event in San Francisco. Their conversation there was perfunctory. Wozniak, by contrast, was effusive when the pair last met, at a convention in San Jose. “He came across the room at me like a long-lost brother. Woz can approach me, but I can’t approach Woz. It’s simply the reality of how you deal with people when they’re phenomenally wealthy and you are not.”
Wayne nevertheless stands by the decision he made in 1976. “I separated myself from the enterprise,” he says. “Nobody ever diddled me out of anything. On several occasions over the next three years Jobs and I had lunch together, he offered me positions at Apple and I always declined.”
Today Wayne supplements his pension by dealing in collectors’ stamps and coins to his neighbours. His passion project is a new slot machine design, for which he’s been trying to attract funding for the past 10 years. His own gambling habit is modest, though. “It’s just a pastime,” he says. “I’m not a serious gambler – I’m too gutless for that!”
Posted by peiper
Filed Under: • Computers and Cyberspace •
• Comments (0)
 Monday - November 11, 2013
Monday - November 11, 2013
FIFY, hundreds of millions saved
3 kids rewrite ObamaCare over the weekend for fun ... and now it works.
Holy ass burgers.
Even as President Obama has issued a constant refrain of how upset he is that his Obamacare website doesn’t work and promises that he’s on top of the fix, three 20-year-old website designers in San Francisco made a working Obamacare website using Healthcare.gov’s own code. They did it in only three days.
The three web developers who created the site, HealthSherpa.com, programmed it to do much of what Healthcare.gov, the Obamacare website, is supposed to do.
The enterprising young men whipped up their version of Obamacare in just days working in their off time.
Unlike the Obamacare website, Ning Liang, George Kalogeropoulous and Michael Wasser’s new site shows Americans the info they really want to see. Signing onto their site will show visitors healthcare plans and pricing that is available. All you do is enter your zipcode, and there it is.
The three are continuing to tweak their site to give visitors even more information, too. Just after their site went live, they added a section that will help visitors find out if they qualify for a tax subsidy.
The only thing the site doesn’t do is connect visitors directly to the insurance companies so that visitors can actually buy a policy.
So these three guys can create a website that does the same sort of things that the Obamacare website is supposed to do and they did it in only a few day’s time? Yet Obama has struggled for years to create a broken, mess of a site that no one can use?
Two thirds of a billion down the drain for shit, and three CHILDREN can fix it in a weekend, just for shits and giggles? Notice that they’re being called “web developers” out of politeness, but these 3 aren’t even in college. They’re just kids ... with ZERO actual professional experience as programmers, debuggers, or testers. And no, they didn’t re-write the code from the ground up; they merely looked at it and figured out how it ought to have been put together in the first place. Which is FAR MORE than the folks doing the actual coding could do. So let’s call this a massive step in the right direction.
And yeah, it may only do 80% of what the “real” program can do ... but it can do it at a cost of ZERO. After 72 hours of tweaking. 3 kids did for free in a couple days what hundreds? of Canadians couldn’t do in years, not even for more than half a billion dollars.
So what I want to know is, when do the arrests start for this massive fraud? After $643 million wasted over years, I think we deserve a mighty grand Perp Walk don’t you? Because we’ve been robbed. And then let’s get at least $625 million back. Strip their assests and send them to jail to rot.
Posted by Drew458
Filed Under: • Computers and Cyberspace •
• Comments (4)
 Wednesday - October 30, 2013
Wednesday - October 30, 2013
a high-profile figure in the Scottish Occupy movement hacks usa military and nasa.
Well here go again.
I guess it’s not too hard for someone like myself, who has a million miles to go to even hope he can understand puters, to be critical of the security exhibited by American military interests. It’s because I have mistakenly had this vision you see, of American tech know how and till recent times our technical invincibility. My excuse, or a better word would be explanation, is that I’ve had too much pride in our abilities and not really knowing enough about computers and how things work, basics aside, I just assumed that our tech people did.
This is getting way outta hand people, and I confess I’m way frustrated. I guess our puter ppl are even more so.
Gee whiz ... after that wikileaks snot and faggot Manning and then Snowden ... here we are yet again with egg on our face and an open back door to sensitive info stored on American computers. In fact, this scummy creep who I dearly wish somebody would kill, slowly, drip by bloody drip, has bragged about his attacks and was planning quite a bit more. Hate doesn’t even begin to describe what I feel.
So here .... in a nutshell, is the story,
His name is Lauri Love. For real, that’s his name.
Lauri Love, an activist in the Occupy movement, is alleged to have stolen ‘massive amounts’ of confidential information – including details of military servicemen – by breaking into thousands of computers.
The 28-year-old from Stradishall, Suffolk, is said to have bragged in messages with his co-conspirators:
‘You have no idea how much we can f*** with the US government if we wanted to’.He seems to brag about infiltrating Nasa networks. He allegedly wrote: ‘lol Nasa. Ahaha, we owning lots of Nasa sites. I think we can do some hilarious stuff with it.’
In another post, he wrote: ‘This stuff is really sensitive. It’s basically every piece of information you’d need to do full identity theft on any employee or contractor for the [government agency].’ It is claimed that Love, who used the online pseudonyms ‘nsh’, ‘route’, ‘peace’, ‘shift’ and ‘love’, planned to use social media, including Twitter, to publicise the attacks.
In one message he planned to announce an attack ‘so it rolls along the morning news in US and gets Europe for the afternoon and evening.’
Love was a leader in protests at Glasgow University, where he was a student. He helped organise demonstrations including a sit-in as part of a protest against cuts to higher education.
He is also believed to have been a high-profile figure in the Scottish Occupy movement, part of the protests which swept throughout much of the world in 2011, and has been pictured at Occupy marches.
Love, who is believed to have studied physics, maths and computing, was apparently involved in 2011’s ‘Hetherington House Occupation’, in which dozens of protesters took over an unused university building in Glasgow and stayed there for seven months.
The charges against Love were filed at the federal court in Newark, New Jersey, because he allegedly used a server in the state as part of his activities. He also faces charges in Virginia for other alleged intrusions.
Either we need to hire these sorts of scum or else kill them.
Here’s the headline as it is online. Not posting the whole article ... use link if interested.
British Baptist minister’s son, 28, who ‘keeps to himself’ charged with hacking into top secret US Army databases, Nasa, and other government agencies
Lauri Love from Stradishall, Suffolk arrested by National Crime Agency
Love, 28, described in court papers as ‘sophisticated and prolific hacker’
Charges follow a joint operation by a number of international police forces
He could be extradited to US where if convicted he faces 10 years in jail
Love has previously been a leader in the Occupy protest movementBy John Stevens, Daniel Bates and Hugo Gye

Love could be extradited to the US, where if convicted he faces up to ten years in prison and a fine for twice the damage caused.
The US government said Love worked with two other people in Australia and one in Sweden – who have not been charged – ‘to disrupt the operations and infrastructure’ of the federal government.
From October 2012 until July this year it is claimed he hacked into thousands of government computer systems – including those of the US Army, US Missile Defense Agency and Nasa – and left behind ‘back doors’ through which he could return to get sensitive data.
The hacking ‘substantially impaired the functioning of dozens of computer servers’ and caused ‘millions of dollars in damage’ to government agencies, according to the indictment.
Posted by peiper
Filed Under: • Computers and Cyberspace • Crime • REALLY WORTHLESS and PUTRID PEOPLE • UK • USA •
• Comments (0)
 Thursday - October 24, 2013
Thursday - October 24, 2013
Free stuff for Macs
In this case, it’s the new OS 10.9 Maverick. I wasn’t going to buy it because every time I upgrade some favorite third-party apps no longer work. I have an external hard drive dedicated to OS 10.6 Snow Leopard because most of my graphic and video editing programs no longer worked when I upgraded to OS 7 Lion. So when I’m doing serious graphic and video editing I just reboot off the external drive.
But I don’t have to buy Maverick — it’s free! at the App Store. Be warned, it’s a 4Gb download; it’s taking awhile. I don’t expect it to be done until sometime before midnight this evening. Then I’ll install it and test my favorite apps on it. If I don’t like the results, I’ll just restore everything from my Time Machine backup drive.
Oh sure, I could just download updated versions of all the apps that don’t work… except I can’t. Some are no longer being supported, and I’m not willing to pay (again) for apps I already bought. I’m unemployed (Thanks Obama! That’s some ‘change’ I didn’t need! I ‘hope’ you rot in Hell for millenia!).
Posted by Christopher
Filed Under: • Computers and Cyberspace •
• Comments (1)
Five Most Recent Trackbacks:
Once Again, The One And Only Post
(4 total trackbacks)
Tracked at iHaan.org
The advantage to having a guide with you is thɑt an expert will haѵe very first hand experience dealing and navigating the river with гegional wildlife. Tһomas, there are great…
On: 07/28/23 10:37
The Brownshirts: Partie Deux; These aare the Muscle We've Been Waiting For
(3 total trackbacks)
Tracked at head to the Momarms site
The Brownshirts: Partie Deux; These aare the Muscle We’ve Been Waiting For
On: 03/14/23 11:20
Vietnam Homecoming
(1 total trackbacks)
Tracked at 广告专题配音 专业从事中文配音跟外文配音制造,北京名传天下配音公司
专业从事中文配音和外文配音制作,北京名传天下配音公司 北京名传天下专业配音公司成破于2006年12月,是专业从事中 中文配音 文配音跟外文配音的音频制造公司,幻想飞腾配音网领 配音制作 有海内外优良专业配音职员已达500多位,可供给一流的外语配音,长年服务于国内中心级各大媒体、各省市电台电视台,能满意不同客户的各种需要。电话:010-83265555 北京名传天下专业配音公司…
On: 03/20/21 07:00
meaningless marching orders for a thousand travellers ... strife ahead ..
(1 total trackbacks)
Tracked at Casual Blog
[...] RTS. IF ANYTHING ON THIS WEBSITE IS CONSTRUED AS BEING CONTRARY TO THE LAWS APPL [...]
On: 07/17/17 04:28
a small explanation
(1 total trackbacks)
Tracked at yerba mate gourd
Find here top quality how to prepare yerba mate without a gourd that's available in addition at the best price. Get it now!
On: 07/09/17 03:07
DISCLAIMER
THE SERVICES AND MATERIALS ON THIS WEBSITE ARE PROVIDED "AS IS" AND THE HOSTS OF THIS SITE EXPRESSLY DISCLAIMS ANY AND ALL WARRANTIES, EXPRESS OR IMPLIED, TO THE EXTENT PERMITTED BY LAW INCLUDING BUT NOT LIMITED TO WARRANTIES OF SATISFACTORY QUALITY, MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE, WITH RESPECT TO THE SERVICE OR ANY MATERIALS.
Not that very many people ever read this far down, but this blog was the creation of Allan Kelly and his friend Vilmar. Vilmar moved on to his own blog some time ago, and Allan ran this place alone until his sudden and unexpected death partway through 2006. We all miss him. A lot. Even though he is gone this site will always still be more than a little bit his. We who are left to carry on the BMEWS tradition owe him a great debt of gratitude, and we hope to be able to pay that back by following his last advice to us all:
It's been a long strange trip without you Skipper, but thanks for pointing us in the right direction and giving us a swift kick in the behind to get us going. Keep lookin' down on us, will ya? Thanks.
- Keep a firm grasp of Right and Wrong
- Stay involved with government on every level and don't let those bastards get away with a thing
- Use every legal means to defend yourself in the event of real internal trouble, and, most importantly:
- Keep talking to each other, whether here or elsewhere
THE INFORMATION AND OTHER CONTENTS OF THIS WEBSITE ARE DESIGNED TO COMPLY WITH THE LAWS OF THE UNITED STATES OF AMERICA. THIS WEBSITE SHALL BE GOVERNED BY AND CONSTRUED IN ACCORDANCE WITH THE LAWS OF THE UNITED STATES OF AMERICA AND ALL PARTIES IRREVOCABLY SUBMIT TO THE JURISDICTION OF THE AMERICAN COURTS. IF ANYTHING ON THIS WEBSITE IS CONSTRUED AS BEING CONTRARY TO THE LAWS APPLICABLE IN ANY OTHER COUNTRY, THEN THIS WEBSITE IS NOT INTENDED TO BE ACCESSED BY PERSONS FROM THAT COUNTRY AND ANY PERSONS WHO ARE SUBJECT TO SUCH LAWS SHALL NOT BE ENTITLED TO USE OUR SERVICES UNLESS THEY CAN SATISFY US THAT SUCH USE WOULD BE LAWFUL.
Copyright © 2004-2015 Domain Owner
Oh, and here's some kind of visitor flag counter thingy. Hey, all the cool blogs have one, so I should too. The Visitors Online thingy up at the top doesn't count anything, but it looks neat. It had better, since I paid actual money for it.